Technology
Prelude: A Manifesto
Software is fragile.
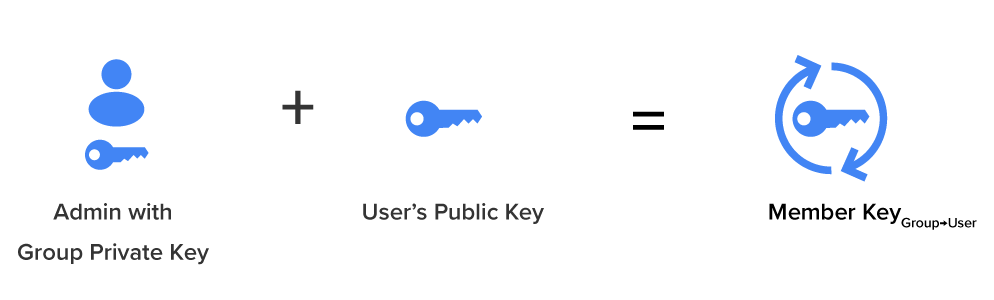
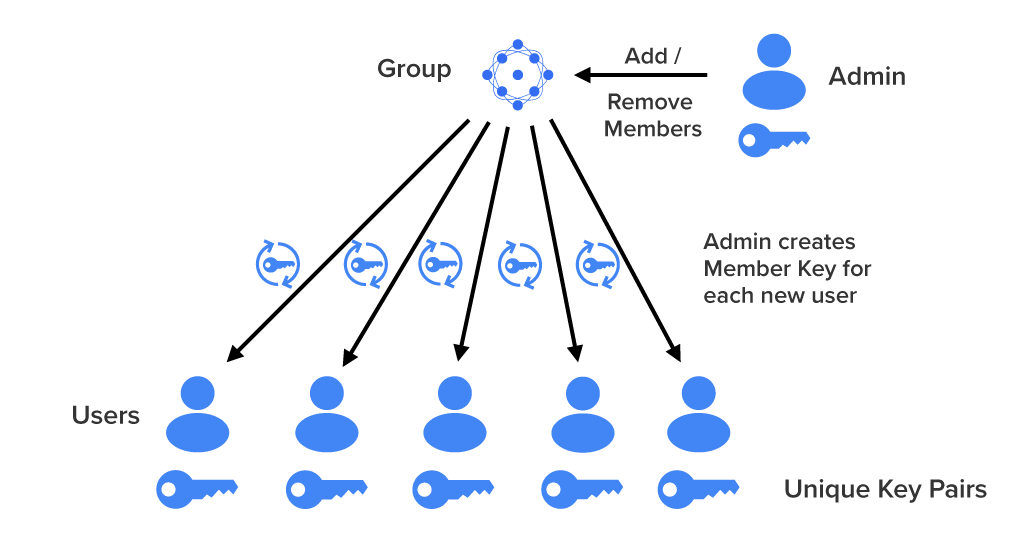
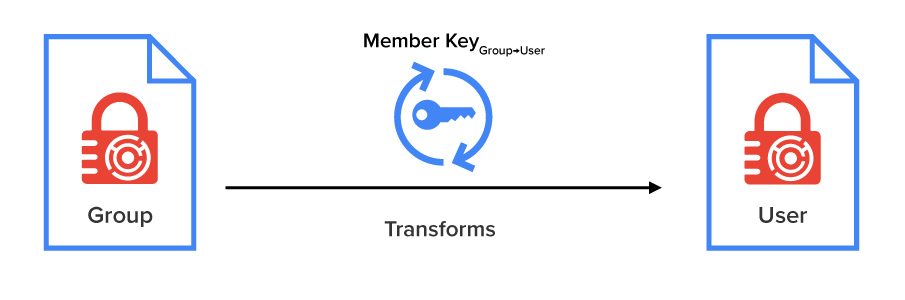
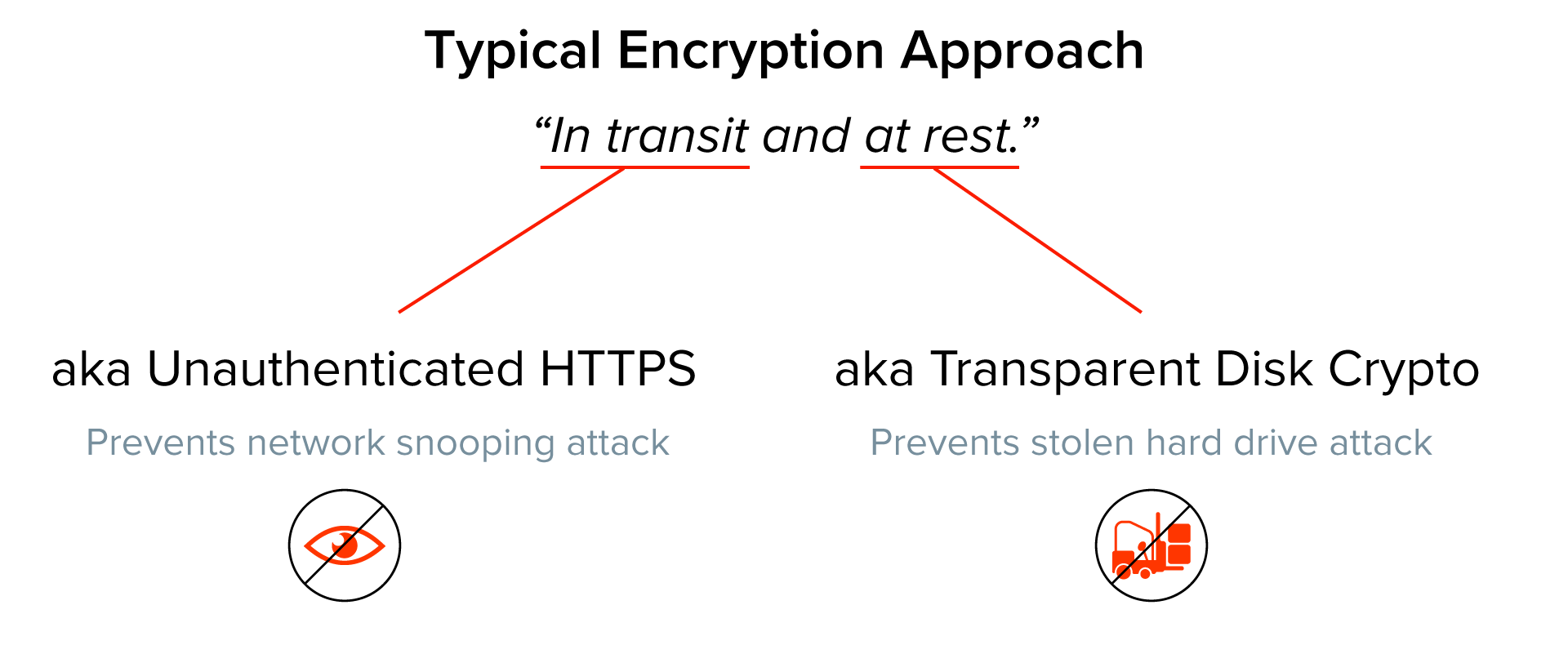
Data is the fuel that powers SaaS. In the rare instances where the data is encrypted, it’s typically just encrypted “in transit and at rest,” which typically translates to “HTTPS and Transparent Disk Encryption.” Sadly, these protections lack cryptographic access controls.
Transparent disk encryption leaves data just as visible to an attacker as to a legitimate user. HTTPS isn’t much better. It stops casual interception of data, but it doesn’t ensure that the person receiving data should be allowed access. It also fails to secure the data at the endpoints.
In short, the standard approach to encryption handles two narrow threats: stolen hard drives and network-level snooping.
Most SaaS companies ignore security concerns when they’re small. As they grow, they add network perimeter technologies like firewalls and intrusion prevention appliances, security incident event management platforms, and staff to monitor them. For B2B SaaS, this evolution is driven by larger customers that demand more intense information security reviews during the sales cycle.
Unfortunately, investing in network perimeter technologies was the solution for a bygone era. Outdated regulations and information security standards assume a network environment of decades past.
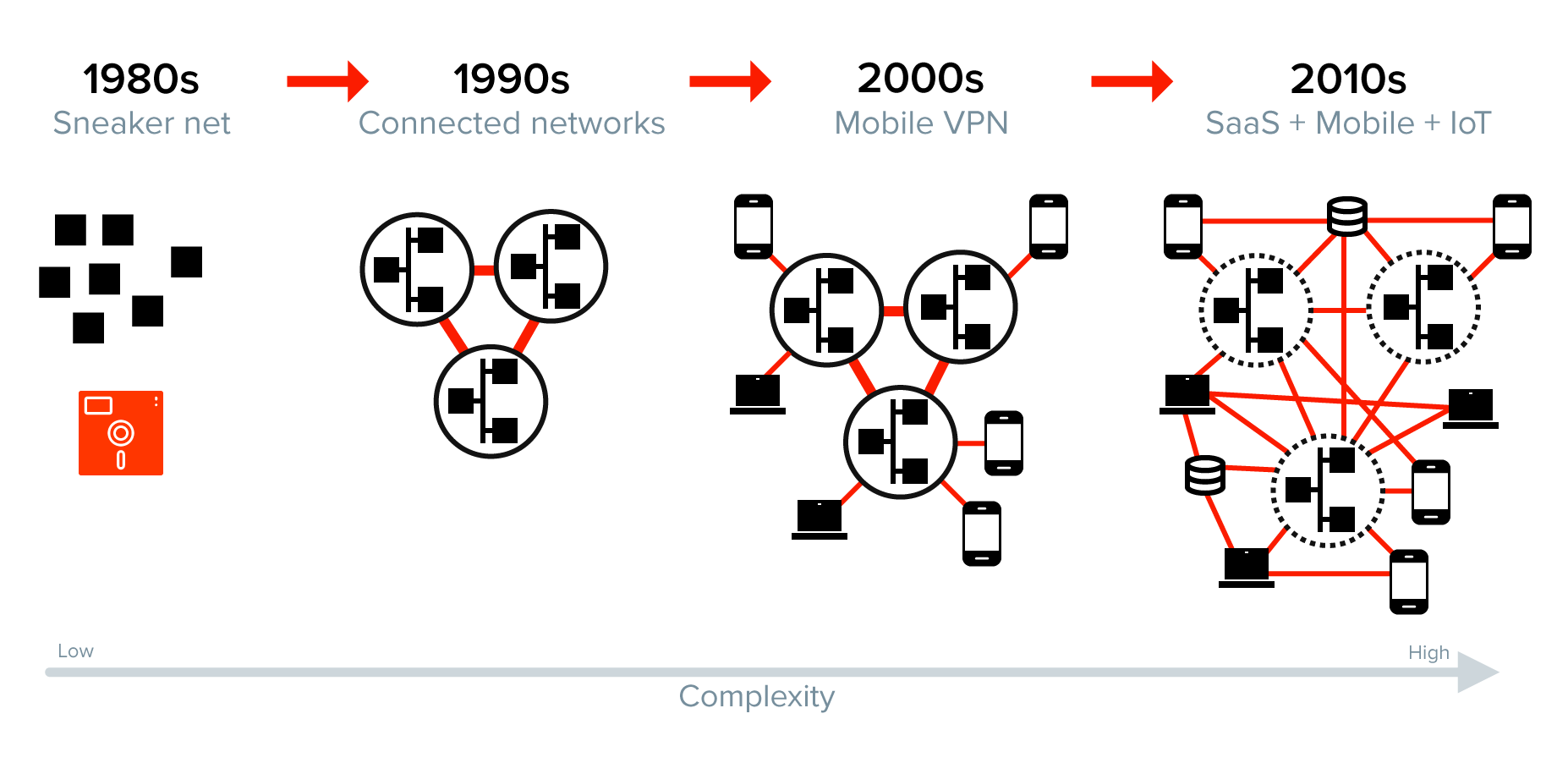
We’ve evolved from walking floppy disks between computers to a world of cloud services, remote employees, mobile devices, IoT, and no clear perimeter that contains the data. The complexity of managing access in this environment is beyond the point where a human can reason about it.